PKI Consortium blog
Posts by tag Vulnerability
The Insecure Elephant in the Room
October 10, 2019 by
Paul Walsh
2FA
Android
Attack
Chrome
DV
Encryption
EV
Firefox
Google
Identity
Malware
Microsoft
Mozilla
Phishing
Policy
Revocation
SSL/TLS
Vulnerability
W3C
The purpose of this article
The purpose of this article is to demonstrate why I believe browser-based UI for website identity can make the web safer for everyone. I explain in great detail, the reasons why the UI and UX didn’t work in the past. And what’s left is only making the problem worse instead of better.
9 Common Myths About CAs
August 1, 2019 by
Tim Callan
(Sectigo)
CA/Browser Forum
CASC
Code Signing
Encryption
ETSI
Identity
Malware
PKI
Qualified
Revocation
SSL/TLS
Vulnerability
WebTrust
Over the years misconceptions about CAs and the SSL infrastructure have arisen. Below is a list of common myths related to SSL and CAs.
Myth #1: CAs are not regulated
Fact: CAs are subject to various checks and balances, including third-party qualified audits through WebTrust or ETSI and strict criteria set forth by leading browsers, before they are accepted in browser root stores. Similarly, the CA/Browser Forum’s Baseline Requirements and Network Security Guidelines establish global standards for certificate issuance and CA controls that will soon be included in third-party auditing standards. Browsers are free to use these requirements to exclude non-compliant CAs from the root store.
The Advantages of Short-Lived SSL Certificates for the Enterprise
July 18, 2019 by
Doug Beattie
(GlobalSign)
CRL
Mozilla
Revocation
SSL/TLS
Vulnerability
Short validity period certificates are becoming ever more common to reduce the scope of data compromised if a server vulnerability is uncovered, such as HeartBleed. Good security practice dictates changing keys on a regular basis, normally annually, but if you want to limit your exposure further, you can replace your certificates and underlying keys more frequently.
Sandstorm is an open source server software that makes it easy to install web apps. In order to solve the problem of setting up DNS without too much complication, Sandstorm announced the release of Sandcats.io. Sandcats.io is a free DNS service which takes 120 seconds to go from an empty Linux virtual machine to a working personal server with a DNS name and HTTPS. The DNS service runs on the sandcats.io server while the “personal server” runs on each individual customers’ computers.
What the Latest Firefox Update Means for SSL Certificates
June 14, 2019 by
Tim Callan
(Sectigo)
CASC
EV
Firefox
SSL/TLS
Vulnerability
Last month marked the release of Firefox 66, the newest iteration of the ever-popular web browser. The update adds a number of interesting new features, including improvements to content loading and extension storage, auto-play sound blocking, and support for the AV1 codec (on the Windows version at least). The search feature has also been improved, and, as is typical of browser updates, a number of known security vulnerabilities have been patched.
2019 – Looking Back, Moving Forward
January 3, 2019 by
Bruce Morton
(Entrust)
Attack
CA/Browser Forum
Certificate Expiry
Chrome
Code Signing
DV
ECC
EV
Forward Secrecy
Identity
Mis-issued
Phishing
PKI
Policy
Qualified
Revocation
RSA
SSL/TLS
TLS 1.0
TLS 1.3
Vulnerability
Looking Back at 2018
2018 was an active year for SSL/TLS. We saw the SSL/TLS certificate validity period drop to 825-days and the mass deployment of Certificate Transparency (CT). TLS 1.3 protocol was finally completed and published; and Chrome status bar security indicators changing to remove “secure” and to concentrate on “not secure.” The CA/Browser Forum has been reformed, the London Protocol was announced and the nearly full distrust of Symantec SSL completed. Here are some details on some of the 2018 happenings in the SSL/TLS ecosystem.
TLS 1.3 Includes Improvements to Security and Performance
April 10, 2018 by
Tim Shirley
Forward Secrecy
IETF
SSL/TLS
TLS 1.2
TLS 1.3
Vulnerability
Last month saw the final adoption, after 4 years of work, of TLS version 1.3 by the Internet Engineering Task Force (IETF). This latest iteration of the protocol for secure communications on the internet boasts several noteworthy improvements to both security and performance:
Security
All cipher suites that do not provide forward secrecy have been eliminated from TLS 1.3. This is a very important security property, because without forward secrecy, if a server’s private key is compromised today, any previously-recorded conversations with that server dating back as long as the key was in use could be decrypted. While it is possible (and highly recommended) to configure a server with TLS 1.2 to prefer (or only support) cipher suites that provide forward secrecy, under TLS 1.3 these are the only option. Other cryptographic modernizations in TLS 1.3 include the elimination of DSA, custom DHE groups, and compression.
Chrome Will Show Not Secure for all HTTP Sites Starting July 2018
February 15, 2018 by
Bruce Morton
(Entrust)
Android
Chrome
Google
HSTS
Phishing
SSL/TLS
Vulnerability
Through 2017 and into 2018, we have seen the use of HTTPS grow substantially. Last Fall Google announced the following status:
- Over 68% of Chrome traffic on both Android and Windows is now protected
- Over 78% of Chrome traffic on both Chrome OS and Mac is now protected
- 81 of the top 100 sites on the web use HTTPS by default
Google helped to drive this growth by implementing the “Secure” and “Not secure” status in Chrome’s status bar. “Secure” was provided for HTTPS sites. “Not secure” was implemented progressively, first resulting for HTTP pages requiring a password or credit card number. Then resulting for HTTP pages where text input was required.
2018 – Looking Back, Moving Forward
January 6, 2018 by
Bruce Morton
(Entrust)
Attack
CA/Browser Forum
CAA
Certificate Expiry
Chrome
ECC
Encryption
Google
Microsoft
Mis-issued
OV
PDF
PKI
ROCA
RSA
SSL/TLS
TLS 1.3
Vulnerability
Looking Back at 2017
2017 saw the end of SHA-1 in public trust SSL/TLS certificates and the start of Certification Authority Authorization (CAA) allowing domain owners to authorize their CA. A “Not secure” browser indication was propagated to push more websites to support HTTPS. There was also a change in the certification authority (CA) ownership with DigiCert acquiring Symantec’s SSL and related PKI business and Francisco Partners buying Comodo’s CA.
2017 – Looking Back, Moving Forward
January 13, 2017 by
Bruce Morton
(Entrust)
3DES
Apple
Attack
CA/Browser Forum
CAA
Chrome
Code Signing
Encryption
Firefox
Google
Identity
Malware
MITM
Policy
Revocation
RSA
SSL 3.0
SSL/TLS
TLS 1.3
TSA
Vulnerability
Looking Back at 2016
Fortunately, 2016 was not a year full of SSL/TLS vulnerabilities. Although some researchers did prove old cryptography algorithms should be put out to pasture. The year showed the end of public-trusted SHA-1 SSL/TLS certificates. It also showed more transparency should be considered due to issues discovered with a few certification authorities (CAs). The great news is HTTPS is no longer the minority — after 20 years, connections using HTTPS has surpassed HTTP.
Stricter Standards for SSL Server Test Coming in 2017
December 13, 2016 by
Bruce Morton
(Entrust)
3DES
CASC
Forward Secrecy
RC4
SSL/TLS
TLS 1.3
Vulnerability
This is a good time to offer a reminder that the CASC has a great tool for secure server testing, the SSL Server Test. The tool grades your server installation and reviews the: certificate, protocol support, key exchange and cipher strength for security against standards and known vulnerabilities.
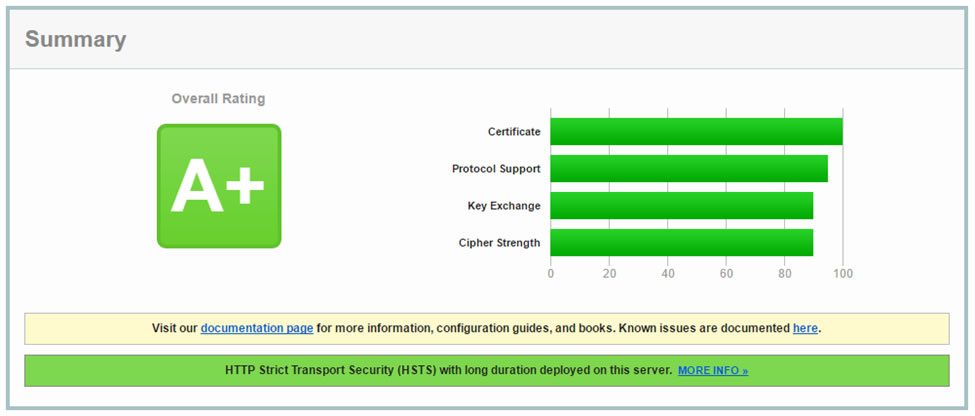
The grading tool also provides feedback on handshake simulations with various versions of browsers and operating systems. This lets the server administrator know which implementations are supported. The test also checks the server mitigation for known vulnerabilities such as: DROWN, BEAST, POODLE and Heartbleed.








































































































































































