PKI Consortium blog
Posts by tag NIST
Preparing for Quantum Computing
April 21, 2020 by
Diana Gruhn
(Entrust)
ECC
IETF
NIST
Quantum
RSA
Quantum computing is advancing, and while experts are not sure when there will be a quantum computer powerful enough to break the RSA and ECC cryptographic algorithms that are currently in use, many are operating under the assumption that this can happen within a 10-15 year timeframe.
New Directions for Elliptic Curve Cryptography in Internet Protocols
June 24, 2015 by
Rick Andrews
ECC
ECDSA
IETF
NIST
RSA
SSL/TLS
Last week I attended and presented at the National Institute of Standards and Technology (NIST) Workshop on Elliptic Curve Cryptography Standards. In NIST’s words, “The workshop is to provide a venue to engage the crypto community, including academia, industry, and government users to discuss possible approaches to promote the adoption of secure, interoperable and efficient elliptic curve mechanisms.”
We began by discussing the reasons for holding this workshop. Speakers acknowledged that although there are no known issues with the current set of NIST curves, in some circles they are widely distrusted. In addition, they are almost 15 years old, not particularly resistant to side-channel attacks, and don’t perform as well as newer curves. For these reasons, many people feel that NIST should standardize on one or more new curves.
Recap of NIST’s Workshop on Improving Trust in the Online Marketplace
April 17, 2013 by
Rick Andrews
CA/Browser Forum
CASC
NIST
Revocation
SSL/TLS
On April 10 and 11, NIST held a workshop in Maryland to bring together many parties (industry, research and academia communities, and government sectors) to examine “technical and administrative efforts to increase trust online by improving the Public Key Infrastructure certificate marketplace supporting SSL and TLS.”
From the opening keynote to the final remarks, we heard from experts around the world. There were presentations on the current state of trust infrastructure and audits, the impact of recent breaches, detailed looks on some emerging solutions like Certificate Transparency and DANE, and new ideas to manage and minimize risk in key usage.
CASC Happenings at NIST
April 10, 2013 by
CA Security Council
CASC
NIST
PKI
Policy
SSL/TLS
TSP
This week members of the CASC will be attending and speaking at the NIST Workshop on Improving Trust in the Online Marketplace. You can also follow the CASC on X for more information and news at @CertCouncil, as well as see some of the presentations after the events on our SlideShare page. Even if you can’t make it to Maryland, you can still watch the event via the live webcast. Please join us for the following CASC member events:
Self-Signed Certificates Don’t Deliver Trust
April 2, 2013 by
Bruce Morton
(Entrust)
CRL
DV
EV
NIST
OCSP
Policy
SSL/TLS
We’ve heard the argument that website operators could just use self-signed certificates. They are easy to issue and they are “free.” Before issuing self-signed certificates, it’s a good idea to examine the trust and security model. You should also compare self-signed certificates to the publicly trusted certification authority (CA) model; and then make your own decision.
Self-Signed Certificate Model
- Owner says who they are
- Owner issues on their own policy
- Owner is responsible for quality
- Owner may not follow industry guidelines
- Owner may not provide certificate status
- Compromised certificates may not be able to be revoked
- Owner is not audited
- Issuer of certificate may not be authorized by the domain owner
- Certificates may not be renewed if there are no reminders
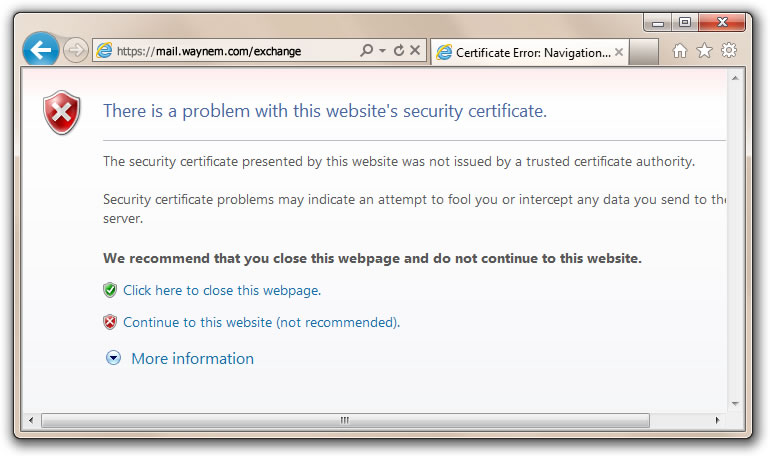
- Self-signed certificate model does not provide trust and the browser provides a trust dialogue box to indicate such
Publicly-Trusted CA-Signed Certificate Model
- CA verifies the owner of the domain and the certificate applicant
- CA operates to a policy in conformance with the requirements of the browser and operating system vendors. The requirements include the CA/Browser Forum Baseline Requirements, Extended validation (EV) Guidelines and recommendations from NIST.
- CA provides quality to the certificate. Checks include compromised keys, minimum key size, ensuring hashing algorithms, maximum validity period and proper certificate extensions.
- CA updates policy based on industry best practices
- CA provides certificate status through CRL and OCSP
- Compromised certificates can be revoked
- CA is audited to certificate issuing criteria such as WebTrust for CA, WebTrust for EV and SSL Baseline Requirements
- Certificate requesters for a Domain validated certificate are authorized by the owner of the domain. Requesters for Organization and Extended Validation certificates are authorized by a member of the organization specified in the certificate.
- CAs provide multiple reminders to ensure the certificates are renewed before they expire. CAs may also provide certificate discovery tools to find certificates on your systems which may not have reminders.
- Publicly trusted CA model is based on the CA being a trusted third party to the browser/OS vendor, the website certificate subscriber and the end-users of the website. The CA is obligated to meet the requirements of all three parties.
So, when should you use a self-signed certificate?
When trust, security, service, quality and reliability are not your criteria.










































































