PKI Consortium blog
Posts by tag 3DES
2017 – Looking Back, Moving Forward
January 13, 2017 by
Bruce Morton
(Entrust)
3DES
Apple
Attack
CA/Browser Forum
CAA
Chrome
Code Signing
Encryption
Firefox
Google
Identity
Malware
MITM
Policy
Revocation
RSA
SSL 3.0
SSL/TLS
TLS 1.3
TSA
Vulnerability
Looking Back at 2016
Fortunately, 2016 was not a year full of SSL/TLS vulnerabilities. Although some researchers did prove old cryptography algorithms should be put out to pasture. The year showed the end of public-trusted SHA-1 SSL/TLS certificates. It also showed more transparency should be considered due to issues discovered with a few certification authorities (CAs). The great news is HTTPS is no longer the minority — after 20 years, connections using HTTPS has surpassed HTTP.
Stricter Standards for SSL Server Test Coming in 2017
December 13, 2016 by
Bruce Morton
(Entrust)
3DES
CASC
Forward Secrecy
RC4
SSL/TLS
TLS 1.3
Vulnerability
This is a good time to offer a reminder that the CASC has a great tool for secure server testing, the SSL Server Test. The tool grades your server installation and reviews the: certificate, protocol support, key exchange and cipher strength for security against standards and known vulnerabilities.
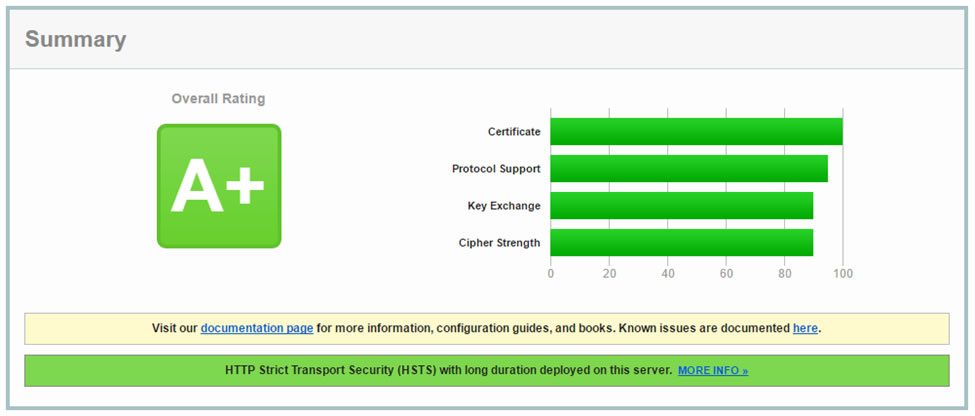
The grading tool also provides feedback on handshake simulations with various versions of browsers and operating systems. This lets the server administrator know which implementations are supported. The test also checks the server mitigation for known vulnerabilities such as: DROWN, BEAST, POODLE and Heartbleed.
How a SWEET32 Birthday Attack is Deployed and How to Prevent It
September 7, 2016 by
Bruce Morton
(Entrust)
3DES
Attack
Encryption
RC4
SSH
SSL/TLS
TLS 1.0
Details surrounding the SWEET32: Birthday attacks on 64-bit block ciphers in TLS and OpenVPN can be found in the paper released by Karthikeyan Bhargavan and Gaëtan Leurent from INRIA in France. The paper shows that cipher suites using 64-bit block length ciphers are vulnerable to plaintext recovery attacks. As such, Triple-DES (3DES) and Blowfish are vulnerable. Here’s an overview.
Vulnerabilities to a SWEET32 Birthday Attack
Certain scenarios are pre-disposed to a SWEET32 Birthday attack. For HTTPS, most susceptible are websites that support the 3DES algorithm and sustain long lived connections.
Perfect Forward Secrecy
April 11, 2014 by
Bruce Morton
(Entrust),
Rick Andrews
3DES
DH
ECC
ECDH
Forward Secrecy
OpenSSL
RC4
RSA
SSL/TLS
TLS 1.2
Recent revelations from Edward Snowden about pervasive government surveillance have led to many questions about the safety of communications using the SSL/TLS protocol. Such communications are generally safe from eavesdroppers, as long as certain precautions are observed. For example, configuring your web server to avoid using SSL2 and SSL3, favoring newer versions of TLS like TLS 1.2, selecting strong ciphersuites, etc.
But even if your server is configured properly, you still must secure the private key associated with your SSL certificate. In nearly all cases, the web site owner generates their key pair and sends only the public key to their Certification Authority (CA). The CA (and any eavesdropper) sees only the public key, and the private key cannot be derived from that. So the CA cannot reveal a web site owner’s private key to the government or an attacker, even if coerced to do so.










































































