Certificate Transparency Deadline Moved to April 2018
May 3, 2017 by
Bruce Morton
(Entrust)
Chrome
Google
IETF
Policy
SSL/TLS
Google just announced they will not be enforcing certificate transparency (CT) logging for all new TLS certificates until April 2018. In a previous blog post, we advised that Google provided a new policy, which required new TLS certificates to be published to the CT logs in order for the domain to be trusted by Chrome.
The reason for the delay was not clear, but Google needs to consider the following:
- Overall CT policy discussions with the major stakeholders are underway, but we are still far away from a conclusion.
- Other browsers appear to be supporting CT, but have yet to determine their policies or advance their browser code.
- The CT deployment document, RFC 6962-bis, tracked by IETF standards has not been released.
- The proposed document for CT Domain Label Redaction that addresses privacy has started, but has not been adopted or completed by the IETF.
- Sufficient, scalable, and reliable CT logs have not been deployed by the ecosystem to address the increase in requirements.
Certification authorities (CAs) as well as TLS certificate subscribers will welcome the extra time to help ensure that deployment of CT logging is efficient and seamless.
The Latest on Certification Authority Authorization
March 21, 2017 by
Jeremy Rowley
Attack
CA/Browser Forum
CAA
Encryption
Identity
OV
PKI
Policy
Qualified
Things are certainly heating up at the CA/Browser with exciting proposals surrounding inclusion of the Wi-Fi Alliance (WFA) as a subjectAltName otherName, new validation methods, and debates over how the CAB Forum will continue operating. One of these newly passed ballots requires all CAs to check and process a domain name’s DNS Certification Authority Authorization (CAA) resource record prior to issuing a digital certificate.
Background
RFC 6844 created CAA records as a method for domain owners to specify a policy on which certificate authorities are authorized to issue certificates for the associated domain. The basic concept is that immediately prior to issuance, the certificate authority (CA) will check the CAA record and determine whether policy permits creation of the certificate. Issuance is permitted if either a CAA record does not exist for the domain or the CAA record lists a string specified by the CA as authorizing the CA to issue the certificate. Using CAA records, the domain owner is able to control policy at a more granular level, including specifying which CA can issue wildcard certificates and how to report issues. Note, that CAA record checking is an additional requirement that occurs after the CA completes the normal domain verification process required by the CA/Browser Forum’s baseline requirements under Section 3.2.2.
2017 – Looking Back, Moving Forward
January 13, 2017 by
Bruce Morton
(Entrust)
3DES
Apple
Attack
CA/Browser Forum
CAA
Chrome
Code Signing
Encryption
Firefox
Google
Identity
Malware
MITM
Policy
Revocation
RSA
SSL 3.0
SSL/TLS
TLS 1.3
TSA
Vulnerability
Looking Back at 2016
Fortunately, 2016 was not a year full of SSL/TLS vulnerabilities. Although some researchers did prove old cryptography algorithms should be put out to pasture. The year showed the end of public-trusted SHA-1 SSL/TLS certificates. It also showed more transparency should be considered due to issues discovered with a few certification authorities (CAs). The great news is HTTPS is no longer the minority — after 20 years, connections using HTTPS has surpassed HTTP.
Stricter Standards for SSL Server Test Coming in 2017
December 13, 2016 by
Bruce Morton
(Entrust)
3DES
CASC
Forward Secrecy
RC4
SSL/TLS
TLS 1.3
Vulnerability
This is a good time to offer a reminder that the CASC has a great tool for secure server testing, the SSL Server Test. The tool grades your server installation and reviews the: certificate, protocol support, key exchange and cipher strength for security against standards and known vulnerabilities.
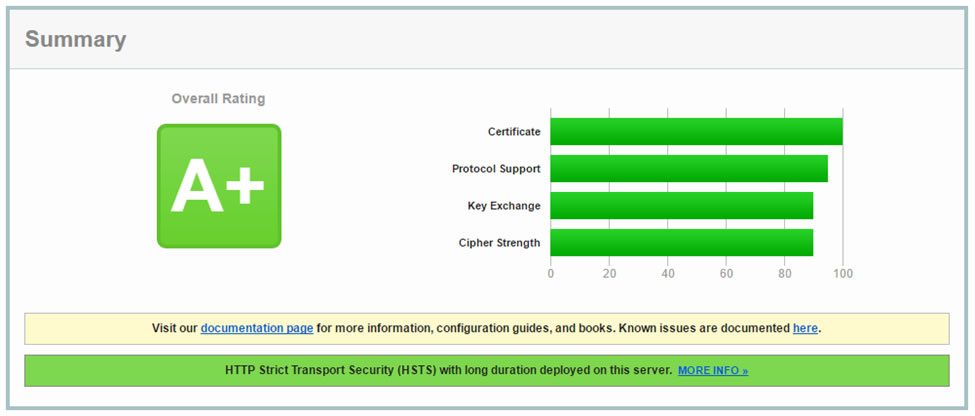
The grading tool also provides feedback on handshake simulations with various versions of browsers and operating systems. This lets the server administrator know which implementations are supported. The test also checks the server mitigation for known vulnerabilities such as: DROWN, BEAST, POODLE and Heartbleed.
Leading Certificate Authorities and Microsoft Introduce New Standards to Protect Consumers Online
December 8, 2016 by
CA Security Council
CASC
Code Signing
FIPS
HSM
Identity
Malware
Microsoft
Revocation
SSL/TLS
TSA
The CASC’s Minimum Requirements for Code Signing Certificates enables a common vetting process for all CAs
San Francisco –December 8, 2016 – the Certificate Authority Security Council (CASC), an advocacy group committed to the advancement web security, today announced the Code Signing Working Group has released new Minimum Requirements for Code Signing for use by all Certificate Authorities (CA). These requirements represent the first-ever standardized code signing guidelines. Code signing is the method of using a certificate-based digital signature to sign executables and scripts in order to verify the author’s identity and ensure that the code has not been changed or corrupted. Helping to verify software authenticity and avoid downloading malware and other malicious software is critical to protecting consumers’ online interactions. Microsoft is the first applications software vendor to adopt these guidelines, with others expected to follow.
The Web Is Moving From HTTP to HTTPS
November 21, 2016 by
Dean Coclin
Chrome
Encryption
Google
SSL/TLS
The four letters, “http”, are known to technical and non-technical users alike as the beginning of any web address. These have been ubiquitous for many years. But things are about to change. Pretty soon, you won’t be able to go to many popular websites just by using those 4 letters. You will need to add an “s” at the end (https). Why is this happening? What are the reasons for this change?
Trust on the Public Web – The Consequences of Covert Action
November 11, 2016 by
Dean Coclin
Apple
Chrome
Firefox
Mis-issued
Mozilla
SSL/TLS
You may have heard in the news that the Chinese Certificate Authority, WoSign, was caught backdating SHA-1 certificates to make it look like they were issued before the December 31, 2015 deadline. Why is this newsworthy? For web-based security to remain an integral part of an ecosystem used every day by millions of people around the world, it all comes down to Trust; trust in the organization issuing the certificates, trust in the browsers that validate and display certificate information to the user, and trust by relying parties browsing web pages secured by certificates. Without trust, worldwide commerce and security on the web are at risk.
Google Certificate Transparency (CT) to Expand to All Certificates Types
November 8, 2016 by
Jeremy Rowley
Announcement
CA/Browser Forum
Chrome
DV
EV
Google
IETF
OV
Policy
SSL/TLS
The policy change goes into effect October 2017
A recent Google announcement stated that all publicly trusted SSL/TLS certificates issued in October 2017 or later will be expected to comply with Chrome’s Certificate Transparency (CT) policy or be untrusted by the browser.
HTTP/2 Update
October 26, 2016 by
Wayne Thayer
Google
SSL/TLS
I wrote about the next version of the HTTP protocol 18 months ago. Since then, HTTP/2 has gained significant traction, but not without generating some controversy along the way.
Performance
Perhaps the biggest question lingering over HTTP/2 relates to real-world performance benefits. A demonstration comparing the time it takes to load a website over HTTP/1.1 without SSL/TLS versus HTTP/2 (which only works in browsers over HTTPS) has been criticized for being unrealistic. It loads 360 unique images, a scenario that highlights the strengths of HTTP/2’s new design. The criticism comes from the fact that the average web page only loads around 100 objects (images, style sheets, etc.), and is often optimized for HTTP/1.1 using techniques that reduce the effectiveness of the HTTP/2 mechanisms.
Why Is Certificate Expiration Necessary?
October 19, 2016 by
Bruce Morton
(Entrust)
Attack
CA/Browser Forum
EV
Hash Function
Identity
OCSP
Policy
RSA
SSL/TLS
Vulnerability
The Long Life Certificate – Why It Doesn’t Exist
Why is certificate expiration even necessary? Wouldn’t it be better if I could just buy a certificate with a long life before expiration? It would really simplify certificate management if it could be installed and forgotten. Simple, no management required, just file-and-forget.








































































































































































