PKI Consortium blog
Posts by author CA Security Council
CASC Announces Launch of London Protocol to Improve Identity Assurance and Minimize Phishing on Identity Websites
June 27, 2018 by
CA Security Council
Attack
CA/Browser Forum
CASC
DV
EV
Identity
OV
Phishing
SSL/TLS
LONDON – (June 27, 2018) – The Certificate Authority Security Council (CASC), an advocacy group committed to the advancement of the security of websites and online transactions, announced at the CA/Browser Forum event in London the launch of the London Protocol – an initiative to improve identity assurance and minimize the possibility of phishing activity on websites encrypted with organization validated (OV) and extended validation (EV) certificates, which contain organization identity information (Identity Certificates).
The London Protocol
June 27, 2018 by
CA Security Council
DV
EV
Identity
OV
Phishing
The objective of The London Protocol is to improve identity assurance and minimize the possibility of phishing activity on websites encrypted by OV (organization validated) and EV (extended validation) certificates (together referred to as “Identity Websites”). The London Protocol reinforces the distinction between Identity Websites making them even more secure for users than websites encrypted by DV (domain validated) certificates. That security feature can then be utilized by others for their own security purposes, including informing users as to the type of website they are visiting and use by antiphishing engines and browser filters in their security algorithms.
Fortify Provides a More Secure Web Experience for Certificates and Smart Cards
June 19, 2018 by
CA Security Council
CASC
Code Signing
S/MIME
SSL/TLS
San Francisco – June 19, 2018 – The Certificate Authority Security Council (CASC), an advocacy group committed to the advancement of web security, today announced that Fortify, an open source application sponsored by the Council, is now available for Windows and Mac. Fortify, a free app, connects a user’s web browsers to smart cards, security tokens, and certificates on a user’s local machine. This allows users to generate X.509 certificates in their browser, replacing the loss of key generation functionality.
Leading Certificate Authorities and Microsoft Introduce New Standards to Protect Consumers Online
December 8, 2016 by
CA Security Council
CASC
Code Signing
FIPS
HSM
Identity
Malware
Microsoft
Revocation
SSL/TLS
TSA
The CASC’s Minimum Requirements for Code Signing Certificates enables a common vetting process for all CAs
San Francisco –December 8, 2016 – the Certificate Authority Security Council (CASC), an advocacy group committed to the advancement web security, today announced the Code Signing Working Group has released new Minimum Requirements for Code Signing for use by all Certificate Authorities (CA). These requirements represent the first-ever standardized code signing guidelines. Code signing is the method of using a certificate-based digital signature to sign executables and scripts in order to verify the author’s identity and ensure that the code has not been changed or corrupted. Helping to verify software authenticity and avoid downloading malware and other malicious software is critical to protecting consumers’ online interactions. Microsoft is the first applications software vendor to adopt these guidelines, with others expected to follow.
Code Signing Baseline Requirements
November 30, 2015 by
CA Security Council
CA/Browser Forum
CASC
Code Signing
Identity
Malware
You may have heard that the CA/Browser Forum is getting ready to approve Baseline Requirements for Code Signing certificates. But why is this important?
Let’s back up and get some background on code signing. Software code that is digitally signed indicates to the user that the code has not been tampered with since it was signed. It also provides authenticity as to who signed it and when. With the advent of malware, it’s important to insure that the code which was written by the developer is the same code which you downloaded and installed into your computer or mobile phone. A digital signature is like a shrink wrap, protecting the code from modification without detection. Second, the code is signed with a digital certificate issued by a public certificate authority which has performed a verification check on the identity of the author. Malware authors don’t like to be identified, hence the likelihood of a legitimate code signing certificate being issued to a malware author is decreased.
How Safe Are Your Business’ Online Payments?: E-Commerce Sites and Protected Payment Gateways
October 21, 2015 by
CA Security Council
Encryption
Google
SSL/TLS
This blog was originally posted on staysafeonline.org on June 29, 2015.
Online payments can be made in a variety of ways, but majority of the online financial transactions are done through secured payment gateways. Secure payment gateways, as the name suggests, are application service providers for ecommerce websites that authorize various financial transactions taking place on online stores for ensuring safety for both the retailers and the online buyers. The key goal of payment gateways is to secure personal information like cconsumers’ credit card numbers by encrypting their personal and confidential information. Learn more about what these gateways are and how they help protect your online transactions.
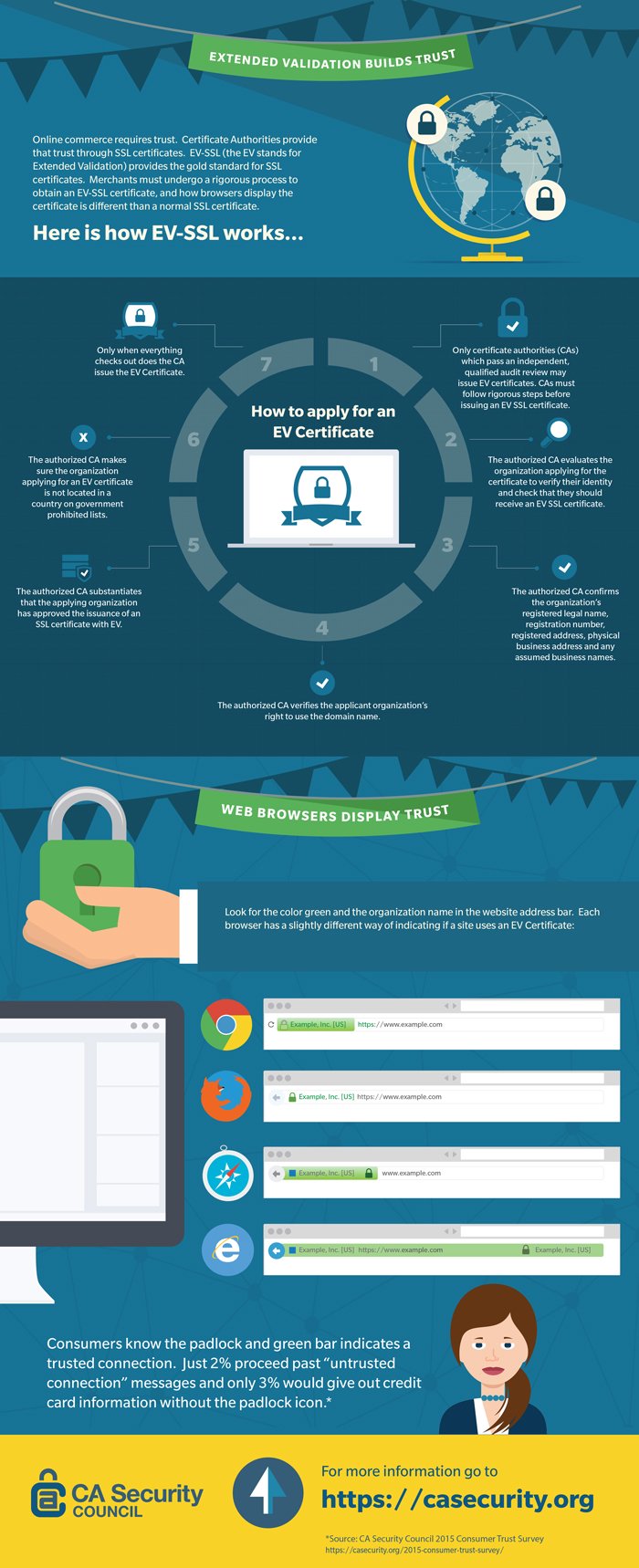
Extended Validation Builds Trust (Infographic)
April 15, 2015 by
CA Security Council
SSL/TLS
Click on the image above to download a full-size version.
CA Security Council Report: Consumers Don’t Know Much About Security, But They Trust the Padlock and Green Bar When Shopping Online
April 13, 2015 by
CA Security Council
CASC
EV
Google
Identity
SSL/TLS
Only 2 Percent Proceed Past “Untrusted Connection” Message
San Francisco – April 13, 2015 – The CA Security Council (CASC), an advocacy group committed to the advancement of the security of websites and online transactions, today released its 2015 Consumer Trust Survey which found that validation matters. While consumers are confused about some aspects of security, they recognize and trust the security that SSL brings to e-commerce sites. Fifty-three percent of respondents identify the padlock as adding confidence in an e-commerce site, with 42 percent associating the green bar and organization name in the URL with greater safety.
Fighting the Good Fight for Online Trust
April 2, 2015 by
CA Security Council
Apple
CAA
CASC
Google
HSM
Mis-issued
MITM
Mozilla
Policy
Root Program
SSL/TLS
WebTrust
Once again Browsers and Certificate Authorities are in the news over the reported mis-issuance of an SSL server certificate to a google.com domain. Discovered by Google most likely via technology known as key pinning and discussed by Google’s Adam Langley in this blog, a Chinese certificate authority, CNNIC (Chinese Internet Network Information Center), apparently issued an intermediate certificate to an Egyptian company called MCS Holdings. Because the CNNIC root certificate is included in the root store of most major browsers, users would not see any warnings on sites that have certificates issued by CNNIC or MCS Holdings. When MCS installed their intermediate into a Man in the Middle (MITM) proxy device, that device could then issue certificates for sites which users connected to that proxy would visit. (MITM is described in more detail in our previous blog here: https://casecurity.org/2015/01/08/gogo-found-spoofing-google-ssl-certificates/)
’Tis the Season for Online Safety
November 30, 2014 by
CA Security Council
SSL/TLS
Vulnerability
The holidays are approaching as quickly as a sleigh pulled by magic reindeer, and every year it seems like the shopping season starts earlier and earlier. In many places, Christmas decorations are now put up before Halloween, ensuring a long and profitable season for merchants. And while most of us have had the experience of opening a disappointing gift on Christmas morning, one thing that can ruin your holiday faster than a homemade sweater is finding out that someone has obtained your credit card number, or compromised your account on your favorite shopping website.