After the news broke that 40 million credit card numbers were stolen from Target in a data breach of epic proportions, many of their customers went to work checking their accounts for fraudulent purchases and replacing cards we’d used recently at Target. These have become standard responses to news of this sort. In much the same way, there are some common actions that you should be aware of if your website becomes compromised.
Many millions of websites are compromised and infected with various forms of malware every year. By one account, more than 10,000 sites are blacklisted by Google every day, meaning that a warning stating “this site may harm your computer” or “this site may be hacked” is displayed when it comes up in a Google search. If this happens to your website, recovery is likely to be your urgent priority, especially if significant customers or revenue are generated by the site. Unfortunately, the recovery process is complex and may take some time. Here we’ll give you an overview and in some cases recommend tools that can help you, but you should also consider engaging a professional.
Verify the Compromise
This step may seem obvious, but today’s malware may not be discovered just by visiting the site because the longer it goes undetected, the more damage it can inflict. Moreover, simply visiting the site to look for malware is possibly the worst thing you can do because you’ll expose your PC to the infection!
If you suspect a compromise, you should check to see if you’re on the Google blacklist. An easy way to do this is to perform a search for your site and look for the telltale warning in the search results as shown below. Another approach is to use Google Search Console.
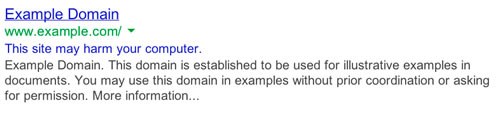
In many cases, your hosting provider can help. You should contact them immediately. A more comprehensive approach is to use a website malware scanner. Similar to a desktop virus scanner, these tools will search your site for malware. The best of these tools will require access to the files on your site via FTP so that source code can be scanned.
Quarantine the Site and Change Passwords
As soon as you determine that your site is infected, you should consider taking it offline until you can clean it up. This step will prevent your site from doing any more harm, and is an especially important consideration if you collect sensitive information from visitors. Even if you decide to keep your site up while it’s being repaired, you should assume that all of your passwords have been compromised and immediately change them.
Assess the Damage
Many states have passed security breach notification laws. If you collect any type of information from your visitors, you should find out if you have any legal obligations and consider consulting an attorney.
This is also a good time to determine if you have a recent backup of your site. Even if you do have a recent backup, consider making another current copy of your compromised site and associated log files. This may be useful in determining the source of the infection or exactly what data may have been taken. Just be careful not to overwrite a backup of your clean site with the backup of the infected files!
Decide How to Fix It
You have a few options at this point:
- Ask your hosting provider for help. Many providers offer this service for a fee
- Subscribe to a malware removal service. Many of the companies that provide website malware scanners are also experts at removing malware from websites. In some cases, they have automated tools that will quickly fix the problems, and in other cases they have a team of people standing by to fix your site.
- Restore a backup. If you’re confident that you have a complete backup of your site that was created prior to infection, restoring it can be an effective solution, as long as you follow additional steps to prevent a recurrence.
- You can also attempt to remove the malware yourself. There are a number of tutorials online that describe the telltale signs of malicious content.
Scan your PC
If the PC you use to maintain your website is infected, this could be the source of your problems. Make sure that your antivirus software is up to date and scanning any system you use when updating your website. This is also a good time to ensure that the latest patches have been installed on your PC(s).
Upgrade Website Software
Another very common source of website infection is vulnerable software. Applications like WordPress are constantly being patched, leaving older versions at risk. You’ll also need to update any plug-ins to the latest versions.
In many cases, your hosting provider will regularly patch your server’s operating system, but if you are using a cloud provider or dedicated hosting environment and have complete control of the operating system (OS), it may be your responsibility and you should apply patches regularly. Applying OS patches monthly is a good practice followed by many IT organizations.
Change Encryption Keys
Once your website has been compromised, you should assume that all content was available to the intruder. This means that your encryption keys need to be replaced to ensure that others can’t intercept your communications. The most common of these keys are the ones used by SSL. Most Certificate Authorities offer a free service that will “reissue” or “rekey” your certificate using a new key pair that you provide via a Certificate Signing Request (CSR). You might also use client certificates for website authentication or keys for SSH access to you site. You should replace all of these keys.
Some applications, including WordPress, use cookies to automatically log administrators into the system. WordPress provides a mechanism by which you can change your secret keys.
Change Passwords Again
Once you are confident that your site is clean, you should again change all passwords. Weak passwords are another very common way that sites are compromised, so you should resolve to use strong passwords. There are many online password generators that can help, and a password safe like LastPass can take most of the pain out of this practice.
Ask Google to Delist Your Site
If your site ended up on the Google blacklist while it was infected, you can log into Google Webmaster Tools, select the website, and ‘Request a review.’ If Google finds that your site is free of malware, the warning should be removed within “a day or so”. A similar process is available for Bing.
Make Sure It Doesn’t Happen Again
We recommend that you regularly scan your website for vulnerabilities that can lead to an infection. The same services that perform website malware scanning will also scan for vulnerabilities. By scheduling recurring vulnerability scans, you will be alerted when new vulnerabilities are found, and will likely be able to fix them by patching software before another infection strikes. An alternative to patching your site is to subscribe to a Web Application Firewall (WAF) service. This will act to protect your site even if vulnerabilities are present.
Finally, this experience will probably leave you with a good sense for the value of making copies of your data. Ensure that your site is being backed up regularly.











































































































